Safety agency ESET is refuting studies that cyberattackers compromised its platforms and used them to focus on clients in Israel with harmful wiper malware. Nonetheless, it did observe {that a} companion there, Comsecure, was impacted.
“We’re conscious of a safety incident which affected our companion firm in Israel final week,” the firm acknowledged on social media platform X. “Based mostly on our preliminary investigation, a restricted malicious electronic mail marketing campaign was blocked inside ten minutes. ESET know-how is obstructing the menace and our clients are safe. ESET was not compromised and is working carefully with its companion to additional examine and we proceed to observe the state of affairs.”
Safety researcher Kevin Beaumont (aka Gossi the Canine) prompted the response after running a blog a couple of malicious electronic mail that an ESET user posted on the ESET person discussion board. The e-mail was flagged as malicious, with the topic line, “Authorities-Backed Attackers Might Be Making an attempt to Compromise Your Gadget!” It presupposed to be from the ESET crew, providing further safety protection within the face of an ongoing assault:
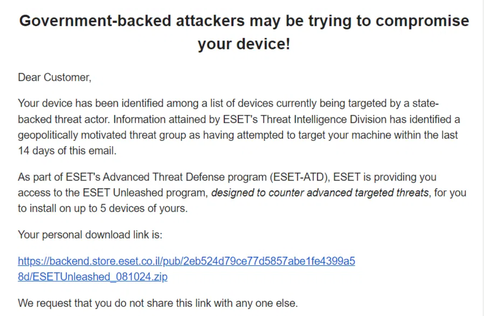
Supply: ESET person discussion board.
The e-mail had a .ZIP attachment that, if opened, unpacked a destructive wiper malware that bears resemblance to that utilized by the Handala threat group, in keeping with the one that flagged the e-mail for Beaumont. Handala, so named for the political cartoon character that has come to personify the Palestinian individuals’s nationwide id, is thought for targeting Israeli organizations with file-destroying wipers within the wake of the Oct. 7 Hamas assaults and ensuing struggle.
Beaumont famous, “I managed to acquire the e-mail, which passes both DKIM and SPF checks for coming from ESET’s retailer,” he mentioned in the blog post. “Moreover, the hyperlink is certainly to backend.retailer.eset.co.il — owned by ESET Israel.”
This led Beaumont to conclude through Mastodon, “ESET Israel undoubtedly acquired compromised, this factor is faux ransomware that talks to an Israeli information org server for no matter motive.”
ESET has now categorically refuted that takeaway, so the idea is that the cyberattackers have been utilizing some type of MO to get around anti-spoofing measures for the e-mail and the .ZIP hyperlink. ESET didn’t instantly return a request for remark from Darkish Studying for extra info on Comsecure’s function within the incident and the assault routine.
The marketing campaign is now blocked for ESET clients.
Source link
#ESETBranded #Assault #Targets #Israel #Agency #Denies #Compromise
Unlock the potential of cutting-edge AI options with our complete choices. As a number one supplier within the AI panorama, we harness the facility of synthetic intelligence to revolutionize industries. From machine studying and information analytics to pure language processing and pc imaginative and prescient, our AI options are designed to boost effectivity and drive innovation. Discover the limitless prospects of AI-driven insights and automation that propel your corporation ahead. With a dedication to staying on the forefront of the quickly evolving AI market, we ship tailor-made options that meet your particular wants. Be part of us on the forefront of technological development, and let AI redefine the best way you use and achieve a aggressive panorama. Embrace the long run with AI excellence, the place prospects are limitless, and competitors is surpassed.






























