AI Tools & Automation
Agentic AI n8n Tutorial in 2025
We built an AI agent within n8n designed to provide investment advice, showcasing the platform’s capabilities for agentic AI. This...
Read moreDetailsTop No-Code ML Platforms: ChatGPT Alternatives in 2025
We benchmarked 4 no-code machine learning platforms across key metrics: data processing (handling missing values, outliers), model setup and ease...
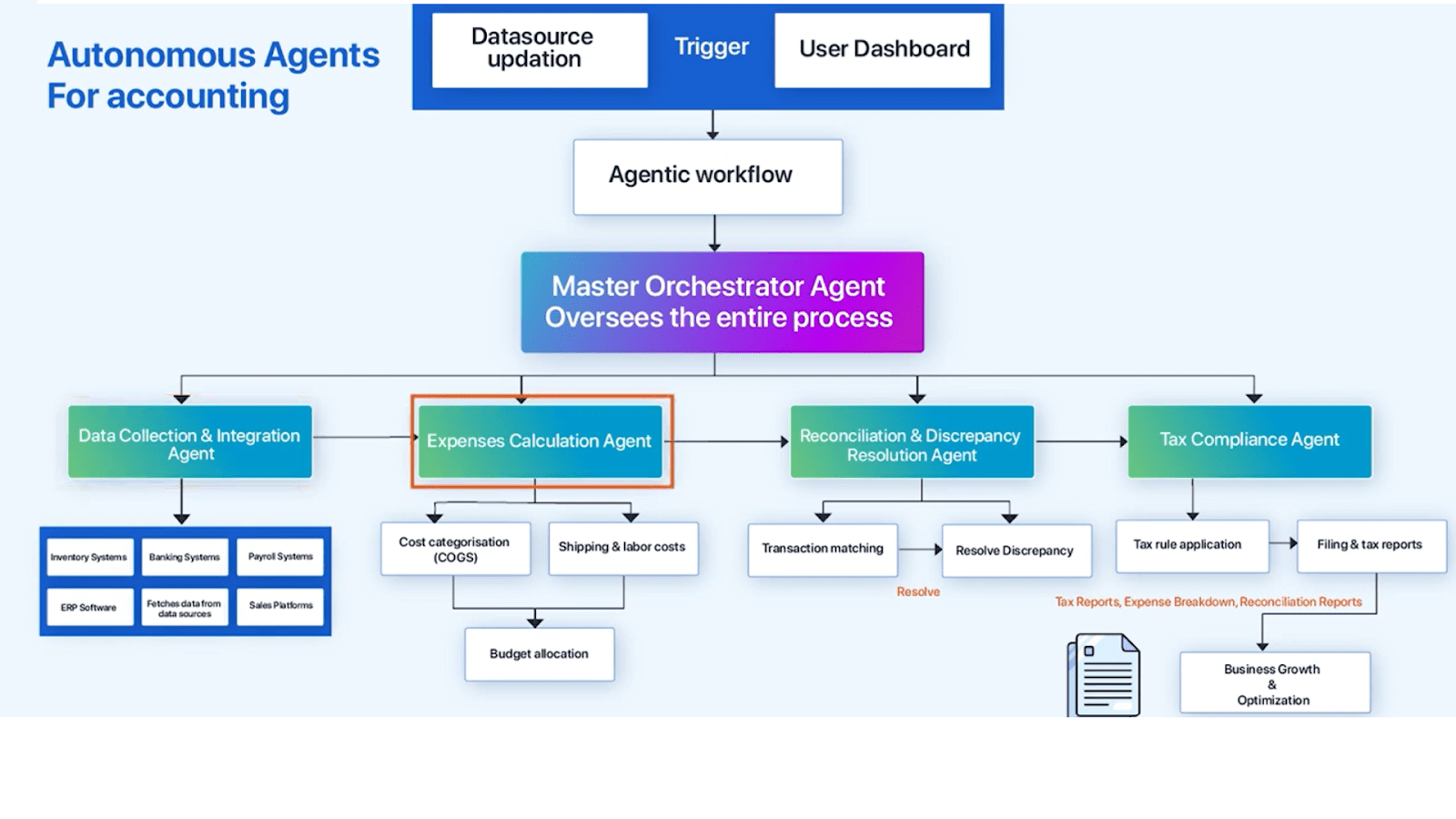
Read moreDetailsCompare 10+ Accounting AI Agents in 2025
Tools like Dext, AutoEntry, and Hubdoc have automated data extraction and transaction posting. But these systems are fundamentally still rule-based,...
Read moreDetailsA Hands-On Review in 2025
As an AI enthusiast, I’ve picked the best generative AI tools for e-commerce content creation. In this review, I’ll showcase...
Read moreDetails5 Social Listening Platforms Benchmark in 2025
We use 5 top social listening tools to help enterprises interested in tracking their online presence, understanding audience engagement, and...
Read moreDetailsWorkload Automation Security: Best Practices & Examples
WLA tools have broad access to systems, credentials, and sensitive data, making them vulnerable targets if left unprotected. Recent security...
Read moreDetailsHow to Build a Claims Processor Agent from Scratch? [2025]
We’ll use Stack AI workflow builder for claims automation and create an AI agent to enable users to upload accounting...
Read moreDetailsFellow, Otter, and TL;DV [’25]
After using Fellow, Otter, and TL;DV for transcription, recording, and summarization of online meetings, I evaluated features, pros, and cons...
Read moreDetailsCloudflare vs Imperva vs Barracuda
Bot management identifies real users, good and bad bots, safeguarding websites, APIs, and digital assets from automated threats. We benchmarked...
Read moreDetailsUse Cases & Examples [’25]
AI agents in healthcare are transforming the way care delivery, diagnostics, operations, and patient engagement work. Unlike traditional software, these...
Read moreDetails



















![How to Build a Claims Processor Agent from Scratch? [2025] How to Build a Claims Processor Agent from Scratch? [2025]](https://i1.wp.com/research.aimultiple.com/wp-content/uploads/2025/05/stack-ai-1.png?ssl=1)
![Fellow, Otter, and TL;DV [’25] Fellow, Otter, and TL;DV [’25]](https://i2.wp.com/research.aimultiple.com/wp-content/uploads/2025/05/note-taker-benchmark.png?ssl=1)

![Use Cases & Examples [’25] Use Cases & Examples [’25]](https://i0.wp.com/research.aimultiple.com/wp-content/uploads/2025/04/sully-1200x630.png?ssl=1)









